A1Z26 Code
The A1Z26 code is a very simple code. As you know, there are 26 letters in the American alphabet so Z would equal 26 because it is the 26th letter in the alphabet.

Abjad
An abjad is a writing system in which only consonants are represented, leaving vowel sounds to be inferred by the reader.
Example
- xmpl
- -x-mpl-
ASCII Code
ASCII is a code used by computers to represent characters as numbers. This allows computers to store a letter as one byte of information. One byte of information allows you to represent 256 different values, which is enough to encode all the letters (uppercase and lowercase) as well as the numbers 09 and other special characters, such as the @ symbol.

Atbash Cipher
The Atbash Cipher is a very specific case of a substitution cipher where the letters of the alphabet are reversed. In other words, all As are replaced with Zs, and Bs are replaced with Ys, and so on. Because reversing the alphabet twice will get you the actual alphabet, you can encipher and decipher a message using the exact same algorithm.
Example

Autokey Cipher
An Autokey Cipher is identical to the Vigenère Cipher with the exception that instead of creating a keyword by repeating one word over and over, the keyword is constructed by appending the keyword to the beginning of the actual plaintext message.
For example, if your plain text message was:
- This is a secret message
And your keyword was “zebra”, then your actual keyword would be:
- zebrathisisasecretmessage
Enciphering and deciphering the message is performed using the exact same method as the Vigenère Cipher.

Baconian Cipher
Francis Bacon created one of the more interesting substitution ciphers. He used two different typefaces slightly differing in weight (boldness). He broke up his ciphertext into five-character groups, each of which would represent one character in his plaintext. Depending on which characters of the group were bold, one could determine the plaintext character using the following table (*stands for a plain character and B for a bold character).

Beale Cipher
A Beale Cipher is a modified Book Cipher. Instead of replacing each word in the secret message with a number, you replace each letter in the secret message with a number.
The letter-by-letter method makes it easier to encode a message with unusual words that may not appear in the book.
With this method, each letter in the secret message is replaced with a number that represents the position of a word in the book which starts with this letter.
For example, if we are enciphering the word “attack” we would start with the letter A. We would find a word in the book that started with A. Let’s say that the 27th word was “and”. The letter A is now translated to 27.
An encoded message may look something like this:
- 713 23 245 45 124 1269 586 443 8 234
It should be noted that for enhanced security, the same number should not be used for the same letter throughout the secret message. Because you have a book, you can pick multiple numbers for each letter and use them interchangeably.
Beaufort Cipher
A Beaufort Cipher uses the same alphabet table as the Vigenère Cipher, but with a different algorithm. To encode a letter you find the letter in the top row. Then trace down until you find the key letter. Then trace over to the left-most column to find the enciphered letter. To decode a letter, you find the letter in the left column, trace over to the key letter, and then trace up to find the deciphered letter. Some people find this easier to do than finding the intersection of a row and column.

Bifid Cipher
The Bifid Cipher uses a Polybius Square to encipher a message in a way that makes it fairly difficult to decipher without knowing the secret. This is because each letter in the ciphertext message is dependent upon two letters from the plaintext message. As a result, frequency analysis of letters becomes much more difficult.
The first step is to use the Polybius Square to convert the letters into numbers. We will be writing the numbers vertically below the message.

The numbers are now read off horizontally and grouped into pairs.
- 41 14 14 31 44 12 13 55 25 42 55 51 25
The Polybius Square is used again to convert the numbers back into letters which gives us our ciphertext: qddltbcxkrxlk.
Since the first letter in the plaintext is encoded into the first and middle letters of the ciphertext, the recipient of the message must have the entire message before they can decode it. This means that if part of the ciphertext is discovered by a third party, it is unlikely that they will be able to crack it.
To decipher a Bifid encrypted message, you first convert each letter into its corresponding number via the Polybius Square. Now, divide the long string of numbers into two equal rows. The digit in the top row and the digit in the bottom row will together reference the decoded letter in the Polybius Square.

Binary Code
The Binary code is a code that computers recognize using only 1s and 0s.

Book Cipher
A book Cipher uses a large piece of text to encode a secret message. Without the key (the piece of text) it is very difficult to decrypt the secret message.
To implement a book Cipher, each word in the secret message would be replaced with a number that represents the same word in the book. For example, if the word “attack” appeared in the book as word number 713, then “attack” would be an encoded message that looked something like this.
- 713 23 245 45 124 1269 586 443 8 234
To decipher the message you simply count the number of words in the book and write down each one.
Braille
Braille is what blind people read. It is a series of raised dots that tell you what letter, number, or word it is.

Caesar Cipher
Because each letter is shifted along in the alphabet by the same number of letters, this is sometimes called a Caesar Shift.
When a letter in the message has a direct translation to another letter, frequency analysis can be used to decipher the message.
For example, the letter E is the most commonly used letter in the English language. Thus, if the most common letter in a secret message is K, it is likely that K represents E. Additionally, common word endings such as ING, LY, and ES also give clues. A brute-force approach to trying all 25 possible combinations would also work to decipher the message.
Example
In this example, each letter in the plaintext message has been shifted 3 letters down in the alphabet.

Columnar Transposition Cipher
In a Columnar Transposition, the message is written out in rows of a fixed length. The message is then read out column by column, where the columns are chosen in some scrambled order. The number of columns and the order in which they are chosen is determined by a keyword.
For example, the word ZEBRAS is 6 letters long. Therefore, there are 6 columns that will be read off in the following order: 6 3 2 4 1 5. The order is chosen by the alphabetical order of the letters in the keyword.
Regular Case
In a regular Columnar Transposition Cipher, the empty spaces are filled with random letters.
For example, suppose we use the keyword ZEBRAS and the message WE ARE DISCOVERED FLEE AT ONCE. Our grid would look like this:

The six columns are now written out in the scrambled order defined by the keyword:
- EVLNE ACDTK ESEAQ ROFOJ DEECU WIREE
Irregular Case
In the irregular case, the empty letters are not filled in with random letters.

The results in the following (shorter) ciphertext:
- EVLN ACDT ESEA ROFO DEEC WIREE
To decipher it, the recipient has to work out the column lengths by dividing the message length by the key length. The step is slightly more difficult if the irregular Case is used. After determining the number of columns, the message can be written in columns and rearranged back into the plaintext message.
Double Columnar Transposition
To make the message even more difficult to decipher, you can take the ciphertext produced by this algorithm and run it through the encryption again using a different keyword. This transposes the columns twice and makes the message extremely difficult to decipher.
Dice Cipher
The Dice Cipher is not dice, it’s just squares with dots in certain places.

Example

Digraph Cipher
Example
- “IA MT RY IN GT OE XP LA IN TH IS” = “VG ZN EI VT TN BC KR YG VT GZ VO”
To decipher it, the decoded letters will be in the coordinates.

Four Square Cipher
The Four Square Cipher uses four 5 by 5 matrices arranged in a square. Each of the 5 by 5 matrices contains the letters of the alphabet (usually omitting “Q” or putting both “I” and “J” in the same location to reduce the alphabet to fit). In general, the upper-left and lower-right matrices are the “plaintext squares” and each contains a standard alphabet. The upper-right and lower-left squares are the “ciphertext squares” and contain a mixed alphabetic sequence.
To generate the ciphertext squares, one would first fill in the spaces in the matrix with the letters of a keyword or phrase (dropping any duplicate letters), then fill the remaining spaces with the rest of the letters of the alphabet in order. The four square algorithm allows for two separate keys, one for each of the two ciphertext matrices.
In the example, “EXAMPLE” and “KEYWORD” have been used as keywords.
To encrypt a message, you would first split the message into digraphs. “This is a secret message” would become:
- TH IS IS AS EC RE TM ES SA GE
Once that was complete, you would take the first pair of letters and find the first letter in the upper-left square and the second letter in the lower-right square. In this example we are enciphering TH, so we locate T and H in the grid below (see blue characters). Now, we find the intersections of the rows and columns of the plaintext letters. In this example, they have been highlighted in red (R and B). These new letters are the enciphered digraph (RB).
You continue enciphering digraphs in this way until you reach the end of the message. To continue our example, “This is a secret message” would be enciphered as:
- RB CP CP AL AO TE RI AS NY FE

Homophonic Substitution Cipher
The Homophonic Substitution Cipher is a substitution cipher in which single plaintext letters can be replaced by any of several different ciphertext letters. They are generally much more difficult to break than standard substitution ciphers.
The number of characters each letter is replaced by is part of the key.
For example, the letter “E might be replaced by any of 5 different symbols, while the letter “Q” may only be substituted by 1 symbol.
The easiest way to break standard substitution ciphers is to look at the letter frequencies. The letter “E” is actually the most common letter in English, so the most common ciphertext letters will probably be “E” (or perhaps “T”). If we allow the letter “E” to be replaced by any of 3 different characters, then we can no longer just take the most common letter, since the letter count of “E” is spread over several characters. As we allow more and more possible alternatives for each letter, the resulting Cipher can become very secure.
Example
Our cipher alphabet is as follows:
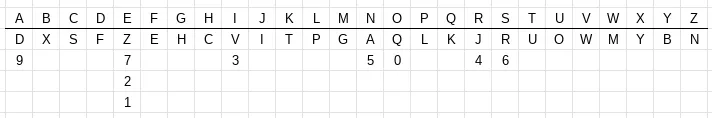
To encipher the message DEFEND THE EAST WALL OF THE CASTLE, we find “D” in the top row, then replace it with the letter below it, “F”. The second letter, “E”, provides us with several choices. We could use any of “Z”, “7”, “2”, or “1”. We choose one of these at random, say “7”. After continuing with this, we get the ciphertext.

The number of ciphertext letters assigned to each plaintext letters was chosen to flatten the frequency distribution as much as possible. Since “E” is normally the most common letter, it is allowed more possibilities so that the frequency peak from the letter “E” will not be present in the ciphertext.
Keyword Cipher
The Keyword Cipher is identical to the Caesar Cipher with the exception that the substitution alphabet used can be represented with a keyword.
To create a substitution alphabet from a keyword, you first write down the alphabet. Below this, you write down the keyword (omitting duplicate letters) followed by the remaining unused letters of the alphabet.

To encipher a plaintext message, you convert all letters from the top row to their corresponding letter on the bottom row (A to K, B to E, etc.).
Morse Code
Morse Code is a method for transmitting information, using standardized sequences of short and long marks or pulses - commonly known as “dots” and “dashes” - for the letters, numerals, punctuation, and special characters of a message.
When using Morse Code, the duration of a dash is equal to the time for three dots. A space between parts of the same letter is equal in duration to one dot. A space between two letters is equal in duration to three dots. A space between the two words is equal to the length of five dots.

One-Time Pad
The one-time Pad is a long sequence of random letters. These letters are combined with the plaintext message to produce the ciphertext. To decipher the message, a person must have a copy of the one-time pad to reverse the process. A one-time pad should be used only once (hence the name) and then destroyed. This is the first and only encryption algorithm that has been proven to be unbreakable.
To encipher a message, you take the first letter in the plaintext message and add it to the first random letter from the one-time pad.
For example, suppose you are enciphering the letter S (the 19th letter of the alphabet) and the one-time pad gives you C (3rd letter of the alphabet). You add the two letters and subtract 1. When you add S and C and subtract 1, you get 21 which is U. Each letter is enciphered in this method, with the alphabet wrapping around to the beginning if the addition results in a number beyond 26 (Z).
To decipher a message, you take the first letter of the ciphertext and subtract the first random letter from the one-time pad. If the number is negative, you wrap around to the end of the alphabet.
Example

Phone Code
The Phone Code is really cool because not a lot of people know it. It is just the number the letter is on and then what number it is on that number.
Example
A is on the 1st number on 2, so it would be 2 1.

Pigpen/Masonic Cipher
The Pigpen Cipher (sometimes called the Masonic Cipher or Freemason’s Cipher) is a simple substitution cipher exchanging letters for symbols based on a grid. For each letter of the plaintext, you would replace it with a symbol corresponding to the section of the key that the letter appears inside.

Playfair Cipher
Memorization of the keyword and 4 simple rules is all that is required to create the 5 by 5 table and use the cipher.
The Playfair Cipher uses a 5 by 5 table containing a keyword or phrase. To generate the table, one would first fill in the spaces of the table with the letters of the keyword (dropping any duplicate letters), then fill the remaining spaces with the rest of the letters of the alphabet in order (to reduce the alphabet to fit you can either omit “Q” or replace “J” with “I”). In the example, the keyword is “keyword”.

To encrypt a message, one would break the message into groups of 2 letters. If there is a dangling letter at the end, we add an X.
For example, “Secret Message” becomes “SE CR ET ME SS AG EX”. We now take each group and find them out on the table. Noticing the location of the two letters in the table, we apply the following rules, in order:
- If both letters are the same, add an X between them. Encrypt the new pair, re-pair the remaining letters, and continue.
- If the letters appear on the same row of your table, replace them with the letters to their immediate right respectively, wrapping around to the left side of the row if necessary. For example, using the table above, the letter pair MD would be encoded as UG.
- If the letters are on different rows and columns, replace them with the letters on the same row respectively but at the other pair of corners of the rectangle defined by the original pair. The order is important - the first letter of the pair should be replaced first. For example, using the table above, the letter pair EB would be encoded as WD.
To decipher, ignore rule 1. In rules 2 and 3, shift up and left instead of down and right. Rule 4 remains the same. Once you are done, drop any extra Xs that don’t make sense in the final message and locate any missing Qs or any Is that should be Js.
Polybius Square Cipher
A Polybius Square Cipher is a table that allows someone to translate letters into numbers. To give a small level of encryption, this table can be randomized and shared with the recipient. In order to fit the 26 letters of the alphabet into the 25 spots created by the table, the letters I and J are usually combined.
To encipher a message, you replace each letter with the row and column in which is appears. For example, D would be replaced with 14.
To decipher a message, you find the letter that intersects the specified row and column.
Example
- Plaintext: This is a secret message
- Ciphertext: 44232443 2443 11 431513421544 32154343112215

Porta Cipher
The Porta Cipher is a polyalphabetic substitution cipher invented by Giovanni Battista della Porta. Where the Vigenère Cipher is a polyalphabetic cipher with 26 letters, the Porta is basically the same except it only uses 13 letters. The 13 cipher letters it uses are reciprocal, so enciphering is the same as deciphering.
The Algorithm
The “key” for a Porta Cipher is a keyword. E.g, “FORTIFICATION”.
The Porta Cipher uses the following tableau to encipher the plaintext.

To encipher a message, repeat the keyword above the plaintext.
- FORTIFICATIONFORTIFICATIONFO
- DEFENDTHEEASTWALLOFTHECASTLE
Now we take the first letter “F” and find it on the first column (the key column containing two letters) on the tableau. Then, we move along the “F” row of the tableau until we come to the column with the “D” at the top (the “D” is the first plaintext letter), the intersection is our ciphertext character, “S”. The same process is repeated for all of the characters.
So, The ciphertext for the above plaintext is:
- FORTIFICATIONFORTIFICATIONFO
- DEFENDTHEEASTWALLOFTHECASTLE
- synnjscvrnrlahutukucvrylany
You may notice that it is possible for two different keywords to produce exactly the same enciphered message. The encryption and decryption process for this cipher is identical, so encrypting a piece of text twice with the same key will return the original text.
Qwerty Code
The Qwerty Code is just the order of letters on a keyboard.

Rail Fence Cipher
In the Rail Fence Cipher, the plaintext is written downward on successive “rails” of an imaginary fence, starting a new column when the bottom is reached. The message is then read off in rows.
For example, if we have 3 rails and a message of “This is a secret message”, you would write out:

The last J is just a random letter to fill in the space. The secret message is then condensed and regrouped.
- TSACTSGHIS RMSEI SEEEA JGURL
To decipher a message, you must know the number of rails that were used to encipher it. You then break up the letters into equal groups. Now you stack the groups on top of each other and read off the message vertically. If you get gibberish, then there are probably some extra letters tacked on the end of the message that are throwing off the grouping. Try removing one letter from the end and try again.
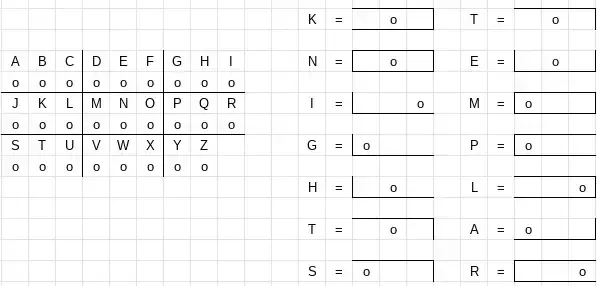
Rosicrucian Cipher
The Rosicrucian Cipher is almost exactly like the Pigpen Cipher. The symbol the letter is inside is the symbol that you put for that letter.
ROT Cipher
The ROT Cipher is when you take a letter and put it back or forth to equal a different letter.
Example
- -1 equals A = Z. +1 equals A = B.
It is relative to the Caesar Cipher.

Route Cipher
A Route Cipher is very similar to a Rail Fence Cipher with one exception. You still write the message vertically in columns, but instead of reading off the secret message horizontally, you read it off using a predetermined pattern.
For example, let’s use a spiral pattern for this one:
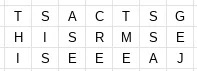
The last J is just a random letter to fill in the space. If we are using a clockwise spiral to read off the message, then it becomes:
- TSACTSGEJAEEESIHISRMSE
A more complex pattern could be, “every other letter going backward to the front and then every other letter going forward to the end again”, which would give you a secret message of:
- JEEISRIGTATSCSHSMESEA
The complex pattern makes this algorithm difficult to decipher unless you know the key.
Running Key Cipher
To encrypt a plaintext message using the Vigenère Cipher, one locates the row with the first letter to be encrypted and the column with the first letter of the keyword. The ciphertext letters is located at the intersection of the row and column. This continues for the entire length of the message.
In a Running Key Cipher, the keyword is the text of a predetermined book or passage. For example, if the chosen book was “A Tale of Two Cities” by Charles Dickens, then the keyword would be:
- It was the best of times, it was the worst of times…
Enciphering and deciphering the message is performed using the exact same method as the Vigenère Cipher.
If the predetermined passage is a string of random letters that are only used once and then discarded, this is similar to a One-Time Pad.

Scytale
A scytale is a cylinder of a specific diameter around which a strip of paper is wrapped.
The plaintext message is written on the paper while it is wound around the stick. Once the paper is unwound, the message becomes difficult to read. To decipher the message, you simply wind the paper around another stick of the same diameter.

Semaphore
To use Semaphore, an operator holds a flag or lighted wand in each hand. The operator extends their arms to the correct position and pauses for each letter of the message. “Attention” is the only signal that involves movement and the “rest” position is the only time when the flags should cross.

Steganography
Steganography is the practice of hiding a message in a place where nobody would think to look. Generally, a steganographic message will appear to be something unassuming, like a picture, an article, a shopping list, or some other message. If you don’t know where to look, you will not even know that a secret message has been hidden.
It may be hidden by using invisible ink between the visible lines of innocuous documents or even written onto clothing. Another method is simply pin-pricking of individual letters in a newspaper article, thus forming a message. It may even be a few words written underneath a postage stamp.
The advantage of steganography over cryptography alone is that messages do not attract attention to themselves, to messengers, or to recipients. An unhidden coded message, no matter how unbreakable it is, will arouse suspicion and may in itself be incriminating.
Examples of Steganography
- Invisible ink
- Concealing messages within the lowest bits of a digital image
- Chaffing and winnowing - Sending multiple conflicting messages, where the recipient has some method of identifying the true message
- Tattoo a message on someone’s head and then let their hair grow back (used in ancient Greece)
- Microdots - Text is written so small that a microscope is required to read it
Tap Code
The Tap Code is a code (similar to Morse Code) commonly used by prisoners in jail to communicate with one another. The method of communicating is usually by “tapping” either the metal bars or the walls inside the cell, hence its name. It is a very simple code, not meant to avoid interception since the messages are sent in cleartext.
It was reportedly invented by four POWs imprisoned in Vietnam and is sometimes called “Smitty Code” after Captain Carlyle (”Smitty”) Harris. Harris remembered an Air Force instructor who had shown him a code based on a 5 by 5 alphabet matrix (a Polybius Square), as shown in the graph.

Each letter was communicated by tapping two numbers. The first designated the horizontal row and the second designated the vertical row. The letter “X” was used to break up sentences and the letter “C” replaced the letter “K”.
For example, to communicate the word “WATER”, the code would be the following:
- ….. .. . . …. …. . ….. …. ..
Because of the difficulty and length of time required for specifying a single letter, most prisoners delivered abbreviations and acronyms for common items or phrases.
Transposition Cipher
Transposition Ciphers can be words written backward.

Trifid Cipher
The Trifid Cipher is the Bifid Cipher taken to one more dimension. Instead of using a 5 by 5 Polybius Square, you use a 5 by 5 by 5 cube. Otherwise, everything else remains the same. As with the Bifid Cipher, the cube can be mixed to add an extra layer of protection, but for these examples we will not be using a mixed alphabet cube.
The first step is to use the cube to convert the letters into numbers. We will be writing the numbers vertically below the message in the order of layer, column, row.

The numbers are now read off horizontally and grouped into triplets.
- 311 213 213 311 112 332 212 111 121 213 212 211 132
The cube is used again to convert the numbers back into letters which gives us our ciphertext.
- sppsdxmabpmjf
To decipher a Trifid encrypted message, you first convert each letter into its corresponding number via the cube. Now, divide the long string of numbers into three equal rows. Now, read off each column and use the cube to convert the three numbers into the alphabet letter.

Vigenère Cipher
To encipher, a table of letters can be used, termed tabula recta, vigenère square, or vigenère table. It consists of the alphabet written out 26 times in different rows, each alphabet shifted cyclically to the left compared to the previous alphabet, corresponding to the 26 possible Caesar Ciphers. At different points in the encryption process, the cipher uses a different alphabet from one of the rows. The alphabet used at each point depends on a repeating keyword.
- ATTACKATDAWN
The person sending the message chooses a keyword and repeats it until it matches the length of the plaintext, for example the keyword “LEMON”.
- LEMONLEMONLE
Each letter is encoded by finding the intersection in the grid between the plaintext letters and keyword letter. For example, the first letter of the plaintext, A, is enciphered using the alphabet in rows L, which is the first letter of the key. This is done by looking at the letter in row L and column A of the Vigenère square, namely L. Similarly, for the second letter of the plaintext, the second letter of the key is used.; the letter of row E and column T is X. The rest of the plaintext is enciphered in a similar fashion.

Decryption is performed by finding the position of the ciphertext letter in a row of the table and then taking the letter of the column in which it appears as the plaintext. For example, in row L, the ciphertext L appears in column A, which is taken as the first plaintext letter. The second letter is decrypted by looking up X in row E of the table; it appears in column T, which is taken as the second plaintext letter.


